Hi all!
Sorry for the lack of news lately, but the holidays got in the middle. First of all, I want to wish all our visitors a stupendous 2009!
Now, regarding pfSense and Layer7, I’m glad to announce that the code is already in the newer 2.0 snapshots. You can find the interface for layer7 rules generation in Firewall->Traffic Shaper. Documentation on how to operate with the layer7 is currently being constructed, and I hope to have it posted soon on the pfSense devWiki.
There are possibly some problems with divert implementation+ipfw-classifyd, so I can not guarantee that it’s going to work right now. But at least, you can have already a look at the work that has been done.
A quick tutorial on how to construct a layer7 container and have it applied to a rule:
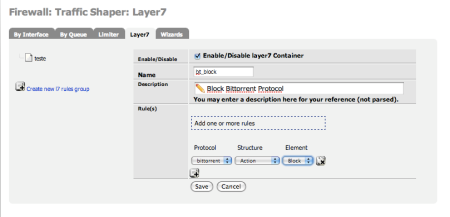
(1) Go to Firewall->Traffic Shaper->Layer7
(2) Create a new rule, assigining it a name, setting it to active and defining what to do with the protocols. For example, there are 3 kinds of structures, but Limiter and Queue will only appear if you have already defined any limiter or queue in the other tabs, next to the layer7 one.
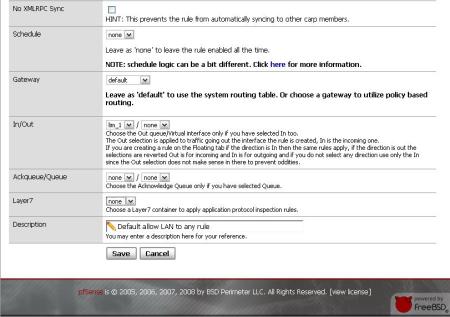
(3) After you create the rule, assign it to a pf rule in Firewall->Rules. Create a new LAN rule and assign the Layer7 Container you created previously (it’s almost in the end of the page).
(4) Report back your problems.
I encourage to report your problems and/or sugestions in the pfSense official forum, and I’ll be very thankfull for the help you all can give in testing this implementation!
P.S: We are working on getting the current shaper wizards to also produce layer7 rules. Stays tunned for more info on this.



 Posted by Helder Pereira
Posted by Helder Pereira